We’re excited to announce the release of version 1.30.0 of FusionAuth. This version shipped on August 12, 2021. 1.30.0 includes a robust Advanced Threat Detection feature, adds 38 webhook events, resolves issues for FusionAuth community members, and more!
This release contained a number of features, enhancements, and bug fixes. Please see the release notes for a full breakdown of the changes between 1.29 and 1.30.0.
There are a few items worth calling out.
JWT Vending Machine
There are scenarios where a user does not yet exist, or is in the process of being created, yet still needs access to services. This may be an anonymous user, who will never authenticate, or a future user, who is using the site, but has not yet authenticated. Imagine a prospective user clicking around a recipe site. They may want to save recipes without signing in. But when they do finally create an account and sign in, they expect their saved recipes to still be attached to their account. In these cases we cannot yet authenticate to FusionAuth.
To address this, the new release includes an API allowing a JWT to be created without a corresponding user.
When you call the /api/jwt endpoint with a JSON payload, you’ll get back a signed JWT, which, when decoded and validated, will look like the below output:
// header
{
"alg": "HS256",
"typ": "JWT",
"kid": "vEp2zjZX45e1SvPuVaZfbkIv_V6vpVPs"
}
// payload
{
"exp": 1629495785,
"iat": 1629495485,
"iss": "piedpiper.com",
"jti": "09c723b1-cb85-4130-bd27-e435eb4f35c3",
"id": "cksknqcp90002au664j1j1cul"
}
If you want to try this out, we wrote a curl script for you, which you need to modify with your own FusionAuth API key, a URL to your FusionAuth app, and a payload of your choosing.
curl -XPOST -H 'Content-type: application/json' -H "Authorization: ..." 'https://local.fusionauth.io/api/jwt/vend' -d '{"claims": {"id":"cksknqcp90002au664j1j1cul", "iss": "piedpiper.com"}, "timeToLiveInSeconds":300}'
Using this ability, a new user on your app can start interacting with the app as a unique user, before needing to create an account. Then, once they do create an account, the unique Id can be used to ensure any saved profile data is retained.
Here’s a video showing how to use this feature.
Threat Detection Feature
Flagging and responding to suspicious behavior is a part of any cybersecurity product, so naturally, we incorporated this functionality into the ever-evolving FusionAuth platform. We created advanced threat detection, a feature that brings best-practice functionality to help you deal with bizarre, possibly malicious behaviour around logins, registrations, user creation, and user updates.
This is a paid feature, available to enterprise-level customers only. If you are already have Enterprise Edition, please open a support ticket requesting this feature be enabled, as we are rolling this feature out over a period of time.
While the entirety of this feature is too large to cover here, we want to call out a few notable aspects.
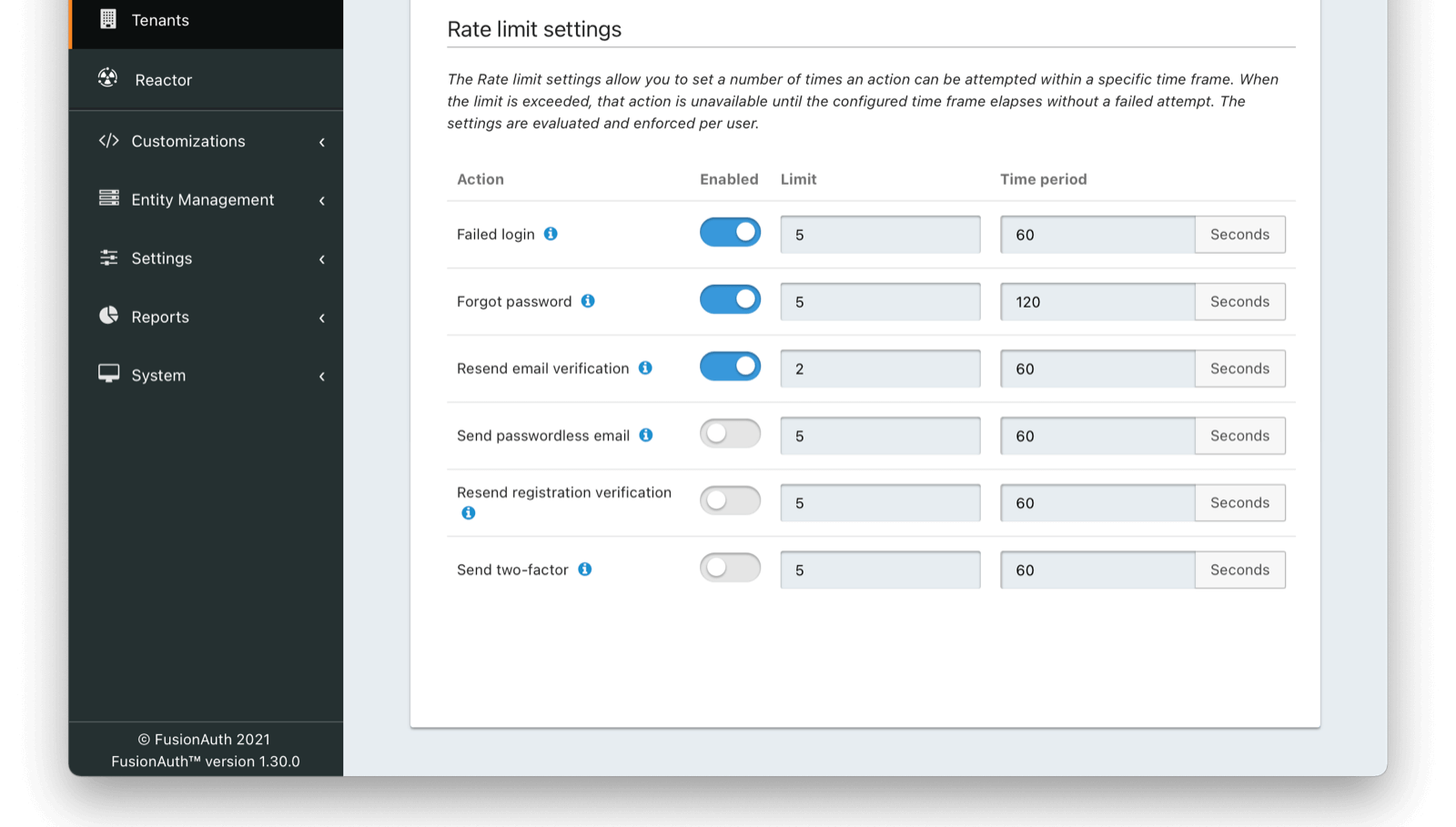
Customizable rate limiting per user for specific requests such as:
- failed login
- forgot password
- send email verification
- and more!
Captcha - Uses additional captcha to guard against brute force attacks.
- Adds a (re)captcha for login pages.
- Includes support for Google ReCaptcha v2, Google ReCaptcha v3, HCaptcha and Hcaptcha Enterprise.
Location aware security
- Inside of every Forgot/Reset Password email that is sent to a user, the geographic location of where the password reset request was made is displayed, so the recipient can identify if the location of the request seems suspicious. (For example: ‘That’s odd..how could I have asked for a password reset in Illinois? I’m in Mumbai!‘)
- Flags suspicious IP addresses on login and sends an email to notify the user of a new login with the IP’s approximate location.
- Calculates ‘impossible travel’ to see if a user could realistically login at different locations around the globe in a reasonable time frame. (This does not provide support if your user is a quantum being…)
- When a login request occurs from an unexpected IP address, a user receives an email to notify them of a new login with an approximate location of the IP address.
Webhooks
- Adds a number of threat detection webhooks to track and respond to important events around passwords, MFA, and login.
To learn more, you can take a look at our release notes.
Webhook Events
We’ve added 38 webhook events to help you monitor what is going on with your app and integrate with other systems. These webhooks cover the entire breadth of creating, updating, and deleting a user, as well as the user registration and password reset lifecycle.
Lastly, we’ve added some webhook events to notify you of the completion of any kickstart files that you run, and also webhooks to audit the behavior of JWTs.
We’re working on the documentation for these webhooks, which will be available here shortly.
The rest of it
Some of the other enhancements and fixes included in this release:
- Search on
oldValue,newValue, andreasonin the Audit Log. - More themed pages have access to the currently logged user using the
currentUservariable. - When an IdP has a linking mode other than Create Pending Link, the token is now stored correctly in the Identity Provider Link object.
- Making an API request to
/api/two-factor/loginwith an empty JSON body, an exception now occurs instead of returning a validation error with a400status code. This has been fixed.
Upgrade at will
The release notes are a guide of the changes, fixes, and new features. Please read them carefully to see if any features you use have been modified.
If you’d like to upgrade your self-hosted FusionAuth instance, see our upgrade guide.
If you have a FusionAuth Cloud deployment, proceed to the “Deployments” tab on your account dashboard and upgrade your servers. If you have any questions about the upgrade, please open a support ticket.
Or, if we’ve piqued your interest and you’d like to use FusionAuth, check out your options.