@uvali Thanks for the feedback, sorry I missed that you'd already used SWAKS.
I'm not sure what is going on because the emails should always be sent if the email server works. If you find out more details, please share.
@dan As I said, I used SWAKS to confirm that Postfix work well.
The issue is that sometimes the messages are sent, sometimes not.
I am not interested to test with Mailcatcher as is a fake SMTP server used only for testing purposes.
Bottom line, I think FusionAuth is a great CIAM product.
Maybe, by installing by RPM package on a RedHat , we will not have this issue.
Thank you for your support.
Hi @dan , unlucky with that, it only works with the same value in
spring.security.oauth2.resourceserver.jwt.issuer-uri=http://localhost:9011/018d6028-e976-7aef-8d35-d65386e6b448/.well-known/openid-configuration
and issuer field in the tenant configuration:
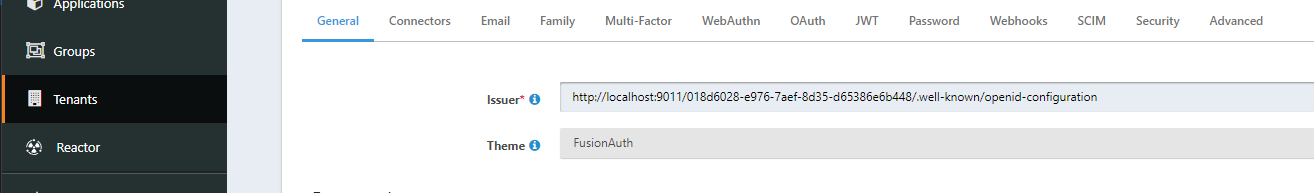
If I change the issuer in the tenant configuration to acme.com in example, http://localhost:9011/018d6028-e976-7aef-8d35-d65386e6b448/.well-known/openid-configuration returns "issuer" : "acme.com" in the response but oauth2 or spring security keeps comparing the token iss with spring.security.oauth2.resourceserver.jwt.issuer-uri property:
"java.lang.IllegalStateException: The Issuer "acme.com" provided in the configuration did not match the requested issuer "http://localhost:9011/018d6028-e976-7aef-8d35-d65386e6b448/.well-known/openid-configuration"
what make sense related with the code in org.springframework.boot.autoconfigure.security.oauth2.resource.reactive.ReactiveOAuth2ResourceServerJwkConfiguration, but from my point of view, the issuer validation should be againt the response not the property
Hiya @youchuan990316 You should be able to do this using javascript. I'm not familiar with particular libraries or methods, but google has a number of options.
You can modify the Account two-factor enable theme page.
Hope this helps.
@uvali Have you tried using SWAKS to confirm that the mail server is working?
Have you confirmed that you have set up the docker network correctly so that FusionAuth is on the same network as the mail server? We have an example with mailcatcher here: https://fusionauth.io/docs/get-started/download-and-install/docker#other-services
@harish_reddy Thanks for the feedback, we appreciate it. While I think it is unlikely we'd separate out those webhooks, you are welcome to add a GH issue with your feedback and we can see how others in the community feel about the topic.
Hiya, welcome to the FusionAuth community!
Hmm, per this doc, you can only use the issuer-uri in specific situations.
To use the issuer-uri property, it must also be true that one of idp.example.com/issuer/.well-known/openid-configuration, idp.example.com/.well-known/openid-configuration/issuer, or idp.example.com/.well-known/oauth-authorization-server/issuer is a supported endpoint for the authorization server. This endpoint is referred to as a Provider Configuration endpoint or a Authorization Server Metadata endpoint.
FusionAuth doesn't support those formats for an arbitrary string. However you could use the tenant id as the issuer, since http://localhost:9011/bafb4319-b7ca-ed27-fa2f-bbdba9d8ec06/.well-known/openid-configuration is a valid endpoint. bafb4319-b7ca-ed27-fa2f-bbdba9d8ec06 is the tenant Id.
Hope that helps.
@mark-robustelli said in How to distinguish between Google Logins and traditional email+pwd logins?:
FusionAuth does have a few "reconcile" lambda's. This might be what you are looking for.
https://fusionauth.io/docs/extend/code/lambdas/google-reconcile.
This is what I'm looking for. Thanks!
These webhooks are often ingested into a SIEM
This is one use case. Agreed.
There might be some applications where UI has to update based on user actions related to MFA on fusionauth pages.
We are using some work arounds for now. But, I think without these webhooks, MFA is incomplete feature.