
Breached password detection best practices
Breached password detection may be the wave of the future, but some third-party solutions are better than others. Performance, flexibility, ease of use, user...
October 19, 2020
Categories

Breached password detection may be the wave of the future, but some third-party solutions are better than others. Performance, flexibility, ease of use, user...
October 19, 2020

Suppose you have an application to which access is so sensitive that if any user's password is found to be breached, the account should immediately be locked;...
August 13, 2020
One common pattern for modern organizations is to centralize user management with a bottleneck architecture. A solid user management system is provisioned and...
July 8, 2020
Hey look! OAuth is getting spiffed up a bit. The original OAuth 2.0 specification was released in October 2012 as RFC 6749. It replaced OAuth 1.0, released in...
April 15, 2020

If you follow us on Twitter (if you don't, you can fix that now) you'll see that we post about data security breaches hitting the internet community. We don't...
April 9, 2019
So you are building an application and you need login and authentication for your users. No problem! Just build a form so the user can submit a username and...
April 4, 2019
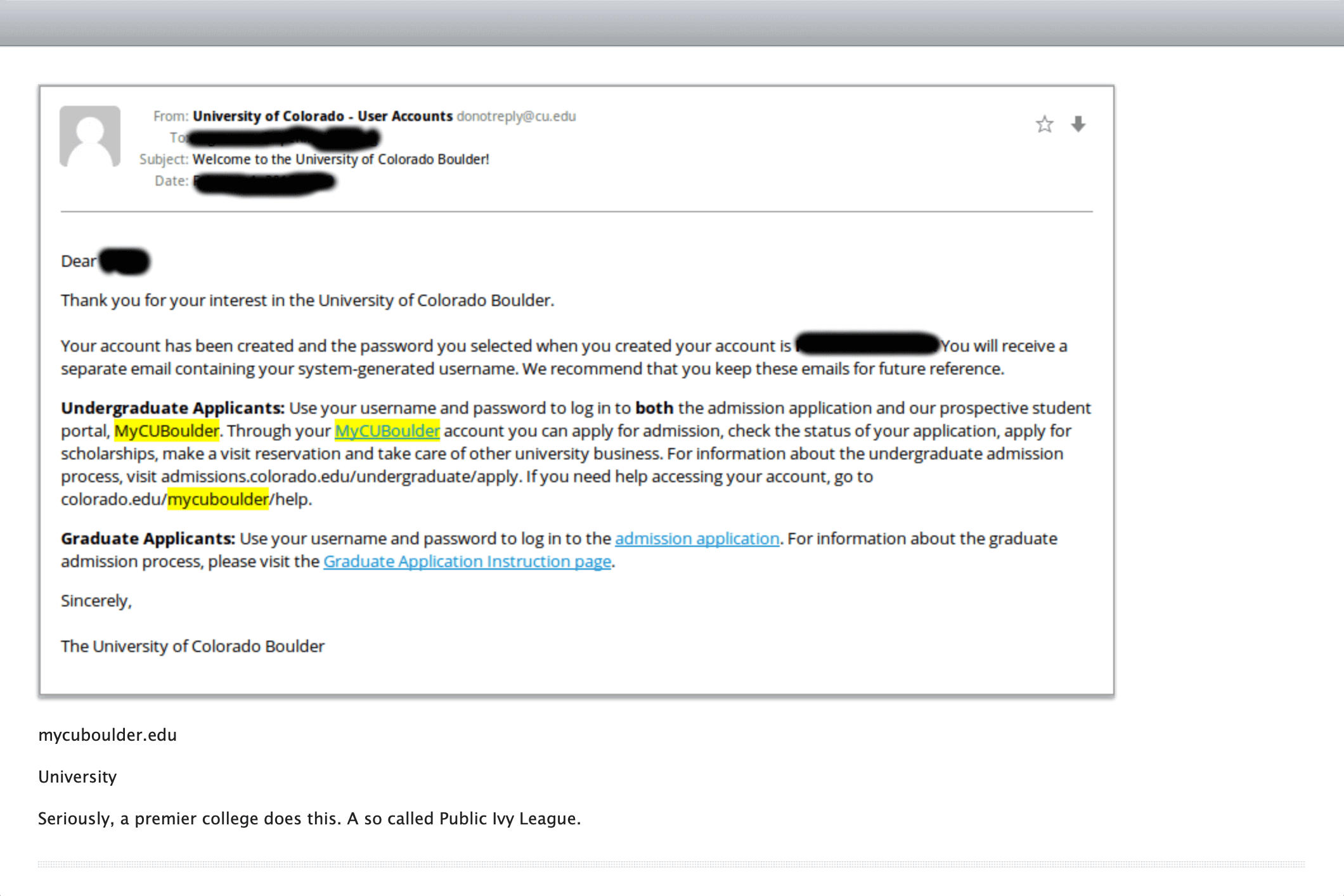
Believe it or not there are still companies emailing users with plaintext passwords. Worse yet, some systems are storing plaintext passwords in the database...
March 12, 2019
A newsletter for developers covering techniques, technical guides, and the latest product innovations coming from FusionAuth.
Just dev stuff. No junk.